Biggest Asian Companies trust RiskImmune™. Biggest Newspapers wrote About us.





Transform the way you manage risk — For every stage of your journey
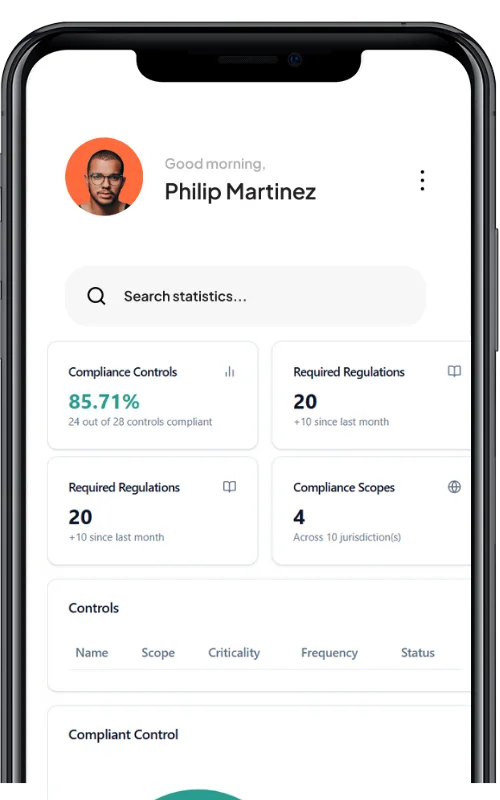
Modern risk management isn’t just about identifying threats — it’s about predicting, preventing, and proving resilience. It means having the tools to monitor, assess, and act on risks in real time — across your vendors, systems, and regulatory obligations. That’s where RiskImmune™ changes the game.
Are you a vendor or supplier? Get discovered—and trusted—faster with our multilingual Trust Center.
Why choose RiskImmune™ ?
Because every organization faces risk differently — and one size never fits all.
RiskImmune™ is more than a platform. It’s a modular ecosystem of AI-powered tools that adapts to your organization’s needs — from fast-growing startups to global enterprises. Whether you’re managing third-party risk, ensuring compliance, or building trust across your ecosystem, RiskImmune grows with you.
No more fragmented solutions. No more data silos. Just one connected suite designed to help you anticipate, assess, and act with confidence.